Latest News

Foto: BleepingComputers
New Microsoft emergency updates fix Windows Server auth issues!
Microsoft has released out-of-band updates to address authentication failures related to Kerberos delegation scenarios impacting Domain Controllers (DC) running supported versions of Windows Server. On impacted systems, end-users cannot sign into services or applications using Single Sign-On (SSO) in Active …
Read More18/11/2021

Foto: BleepingComputers
Here are the new Emotet spam campaigns hitting mailboxes worldwide!
The Emotet malware kicked into action yesterday after a ten-month hiatus with multiple spam campaigns delivering malicious documents to mailboxes worldwide. Emotet is a malware infection that is distributed through spam campaigns with malicious attachments. If a user opens the attachment, malicious macros or…
Read More18/11/2021

Foto: BleepingComputers
Microsoft November 2021 Patch Tuesday fixes 6 zero-days, 55 flaws!
Today is Microsoft's November 2021 Patch Tuesday, and with it comes fixes for six zero-day vulnerabilities and a total of 55 flaws. The actively exploited vulnerabilities are for Microsoft Exchange and Excel, with the Exchange zero-day used as part of the Tianfu hacking contest. Microsoft has fixed 55 vu…
Read More18/11/2021

Foto: BleepingComputers
New Android malware targets Netflix, Instagram, and Twitter users!
A new Android malware known as MasterFred uses fake login overlays to steal the credit card information of Netflix, Instagram, and Twitter users. This new Android banking trojan also targets bank customers with custom fake login overlays in multiple languages. Read more.
Read More18/11/2021

Massive campaign uses YouTube to push password-stealing malware!
Widespread malware campaigns are creating YouTube videos to distribute password-stealing trojans to unsuspecting viewers. Password stealing trojans are malware that quietly runs on a computer while stealing passwords, screenshots of active windows, cookies, credit cards stored in browsers, FTP credentials, a…
Read More27/10/2021

Apple Releases Urgent iPhone and iPad Updates to Patch New Zero-Day Vulnerability!
Apple on Monday released a security update for iOS and iPad to address a critical vulnerability that it says is being exploited in the wild, making it the 17th zero-day flaw the company has addressed in its products since the start of the year.' The weakness, assigned the identifier CVE-2021-30883, conce…
Read More27/10/2021
- FILLING THE ADEQUATE FORM
- WRITE AN EMAIL: reports@kos-cert.org
- BY CALLING: +383 (0)38 212 345
INCIDENT REPORT

How to fix the Windows 0x0000007c network printing error?!
A Windows security update released in October caused widespread Windows 10 and Windows 11 issues where users experience 0x0000007c errors when adding or…

"No More Ransom"
The “No More Ransom” website is an initiative by the National High Tech Crime Unit of the Netherlands’ police, Europol’s Europea…

How to Mitigate Microsoft Windows 10, 11 SeriousSAM Vulnerability ?!
Microsoft Windows 10 and Windows 11 users are at risk of a new unpatched vulnerability that was recently disclosed publicly. As we reported last week, …

Holiday & Travel Booking!
When using the internet to research or book your holiday or other travel arrangements, the world is literally at your fingertips. However, there are ris…

5 Critical Steps to Recover From a Ransomware Attack!
Hackers are increasingly using ransomware as an effective tool to disrupt businesses and fund malicious activities. A recent analysis by cybersecurity …

Firewalls!
Because the internet is a public network, any connected computer can find and connect to any other connected computer. A firewall is a barrier between t…

Social Media Phishing!
It is well-known that email messages, texts and phone calls are methods commonly used by criminals to approach people with the aim of committing financi…

How to Effectively Prevent Email Spoofing Attacks in 2021?
Email spoofing is a growing problem for an organization's security. Spoofing occurs when a hacker sends an email that appears to have been sent from…

Microsoft shares detection, mitigation advice for Azure LoLBins!
Azure LoLBins can be used by attackers to bypass network defenses, deploy cryptominers, elevate privileges, and disable real-time protection on a target…

How to Manage and Secure Active Directory Service Accounts?
There are many different types of accounts in a typical Active Directory environment. These include user accounts, computer accounts, and a particular t…

Ransomware!
Ransomware is a form of malware that gives criminals the ability to lock a computer from a remote location - then displays a pop-up window informing the…

Privacy!
Maintaining privacy whilst online is essential in avoiding identity theft and fraud. Apart from these risks, however, there is personal information abou…

How Does Your AD Password Policy Compare to NIST's Password Recommendations?
End-user passwords are one of the weakest components of your overall security protocols. Most users tend to reuse passwords across work and personal acc…

How to Defend Against Malware, Phishing, and Scams During COVID-19 Crisis?!
Cyber risk management calls for both preventive and detective measures listed below: 1 — Educate Your Staff Most phishing e-mails appear so legi…

How to remove the PBlock+ adware browser extension!
What is PBlock+ adware browser extension? PBlock+ is a Google Chrome extension that claims to be a popup blocker, but instead displays advertisements i…

How to Prevent Pwned and Reused Passwords in Your Active Directory!?
Many businesses are currently looking at how to bolster security across their organization as the pandemic and remote work situation continues to progre…

Cyberbullying!
Online bullying - like bullying in the playground, street or home - can cause child misery. Your child should always tell you if and when this is happen…

Downloading & File Sharing !
Downloading content over the internet is a great way to enjoy music, video, games and other entertainment. Downloading is also a very convenient way to …

How to use ThunderX Decryptor?
A decryptor for the ThunderX ransomware has been released by cybersecurity firm Tesorion that lets victims recover their files for free. To use the decr…

How to fix Windows 10 search problems?!
One of the flagship features of Windows 10 is the built-in search that allows you to search for your local files and Bing. Whether it be due to Windows…

Remove the BipApp Chrome Extension!
What is BipApp Chrome Extension? BipApp by is a Google Chrome extension that has a description of "Search From your address bar with BipApp Search…

Remove the Chrome search contest 2020 Scam!
What is Chrome search contest 2020 Scam? The Chrome search contest 2020 scam is a browser based advertisement that states pretends to be from Google an…

Remove unwanted Windows 10 apps with this new open source tool!
A new standalone utility named Bloatbox has been released that allows Windows 10 users to debloat the operating system by removing unwanted preinstalled…

How to use Windows 10 File History to make secure backups!
With the Windows 10 File History feature, you can back up copies of files and folders to secure locations in the case they are deleted by accident. By …

How to import and backup saved passwords in Google Chrome!
Google Chrome Password Manager lets you save usernames and passwords and automatically use them to log in to websites you visit. If you ever decide t…

Microsoft quietly created a Windows 10 File Recovery tool, how to use!
Microsoft has created a Windows 10 File Recovery Tool that recovers deleted files and forgot to tell anyone. Everyone has deleted a file by accident an…

Safe Browsing!
Just being able to use the internet does certainly not mean that your child has the maturity or experience to handle everything they might find there. …

How to ensure your devices are as secure as possible?!
Devices like smartphones, tablets and PCs are getting more and more secure, but hackers are getting better at attacking them too. So if you've just…

DDoS Attacks!
It is becoming increasingly common for organisations to be hit by online attacks which render their website unable to service legitimate requests. Distr…

Protection Measures for Online Banking!
Banking online is very convenient but you must protect your password and personal details to prevent criminals from accessing your account in your name.…

How to enable the new Google Chrome 83 features now!
Google released Chrome 83 yesterday, and with it came numerous features such as a new Incognito cookie control, a Security check feature, new Security s…

Protecting Against Malicious Code!
What is malicious code? Malicious code is unwanted files or programs that can cause harm to a computer or compromise data stored on a computer. Various…

SPEAR PHISHING PROTECTION MEASURES!
KOS-CERT has been notified of an increase in attack campaigns on information and communication systems and in particular on health systems. Such campaig…

How to help avoid Coronavirus-related scams !
Be wary of approaches from supposed travel agents, tour operators, airlines, cruise companies, insurance companies or compensation firms promising to ar…

Remove the Wisip Chrome Extension !
What is Wisip Chrome Extension? Wisip is a Google Chrome extension that has a description of "This extension configures your Default Search to Sma…

Secure Remote Working During COVID-19 — Checklist for CISOs!
Coronavirus crisis introduces a heavy burden on the CISOs with the collective impact of a mass transition to working remotely coupled with a surge of cy…

How to Secure Your Zoom Meetings from Zoom-Bombing Attacks !
Since countries have begun enforcing shelter-in-place and stay-at-home orders during the Coronavirus pandemic, the Zoom video conferencing software has …

How to handle with the Unpatched Critical 0-Day RCE Flaws Affecting All Windows Versions!
Microsoft said it's aware of the issue and working on a patch, which the company would release to all Windows users as part of its next Patch Tuesda…

How CISOs Should Prepare for Coronavirus Related Cybersecurity Threats!
The Coronavirus is hitting hard on the world's economy, creating a high volume of uncertainty within organizations. Cybersecurity firm Cynet today …

UK NCSC Releases Tips on Securing Smart Security Cameras!
The UK National Cyber Security Centre (NCSC) has released guidance on how to correctly set up smart security cameras and baby monitors to avoid having t…

Using Electronic Devices in Public Places!
When using or carrying your smartphone or tablet in a public place – whether outdoors or in a café, restaurant or in the office – the…

Remove the Flash App+ Chrome Extension !
What is Flash App+ Chrome Extension? Flash App+ is a Google Chrome extension that has a description of "This extension configures your Defau…

Fix a Missing VCRUNTIME140.dll DLL Error in Windows !
If you start a program and receive an error that Windows is unable to find the vcruntime140.dll DLL or that it is missing, you can use this tutorial to …

Remove the Windows Defender Browser Protection Tech Support Scam !
What is Windows Defender Browser Protection Tech Support Scam? The Windows Defender Browser Protection tech support scam is a fake web site alert that …

Social Media Phishing !
It is well-known that email messages, texts and phone calls are methods commonly used by criminals to approach people with the aim of committing financi…

How to Find & View the Files Installed by a Chrome Extension !
Whether it be because you suspect a Chrome extension is malicious, you want to create a backup of a favorite and discontinued extension, or you just wan…

How Organizations Can Defend Against Advanced Persistent Threats !
Advanced persistent threats (APTs) have emerged to be legitimate concerns for all organizations. APTs are threat actors that breach networks and infrast…

14 Ways to Evade Botnet Malware Attacks On Your Computers !
Cybercriminals are busy innovators, adapting their weapons and attack strategies, and ruthlessly roaming the web in search of their next big score. Eve…

How to Use Windows Defender to Scan a Folder for Malware !
Windows 10 comes with a free built-in antivirus program called Windows Defender that offers real-time protection and the ability to performs scans of yo…

INFORMATION ON ADWARE !
A Adware program is one that displays advertisements on your computer or within the program itself. Just because a program is Adware, though, does not m…

4 Best Free Online Security Tools for SMEs in 2020 !
Cyberattacks on small and midsized companies in 2019 cost $200,000 per company on average, mercilessly putting many of them out of business, says CNBC i…

Remove the Power App Chrome Extension !
What is Power App Chrome Extension? Power App is a Google Chrome extension that has a description of "This extension configures your Default Searc…

Remove the HD Video Player PUP !
What is HD Video Player? HD Video Player PUP is a potentially unwanted program that in itself is not malicious, but if installed indicates that you mos…

How to Update Windows 10 Drivers Manually !
Drivers allow Windows to work with hardware components such as graphics card, memory card, storage, camera and other essential components recognized by …

Telephone Banking Fraud
Telephone Banking Fraud is a scam which is becoming increasingly commonplace. The fraudsters do not actually scam their victims online, but use the tele…

Remove the Your Windows 10 is damaged and irrelevant Tech Support Scam !
What is Your Windows 10 is damaged and irrelevant Tech Support Scam? The Your Windows 10 is damaged and irrelevant tech support scam that displays a po…

How to Enable Ransomware Protection in Windows 10 !
Windows Defender includes a security feature called "Ransomware Protection" that allows you to enable various protections against ransomware i…

Remove the IObyte System Care PUP !
What is IObyte System Care PUP? IObyte System Care PUP is a potentially unwanted program that states it scans Windows for Malware/Pup Threats, ways to …

Remove the Genius Search Chrome Extension !
What is Genius Search Chrome Extension? Genius Search is a Google Chrome extension that has a description of "This extension configures your Defau…

Update Your Browser !
It is recommended that for optimum safety and security when using the internet, you always run the latest version of your chosen browser that your opera…

Decrypting eCh0raix /QNAPCrypt encrypted files !
The good news is that security researcher and ransomware expert BloodDolly has released the eCh0raix Decoder in our support topic for this ransomware. U…

Remove the ExtenBro DNS Changing Trojan !
What is ExtenBro DNS Changing Trojan? ExtenBro is a DNS changing Trojan that blocks users from accessing security sites in order to prevent them from d…

Decrypting the LooCipher Ransomware !
If you were infected with the LooCipher Ransomware and still have the encrypted files, simply download the decrypt_LooCipher.exe program from the follow…

Wireless Networks & Hotspots
Wireless networks have revolutionised the way we can use computers and mobile devices, both in the home and office – and when we are out and about…

Mobile Apps !
For many people, apps have become the favourite way to communicate and access the internet through our phones and tablets. We use them to play games, se…

How to Decrypt GandCrab encrypted files !
If you were infected with the GandCrab Ransomware v1, v4, and versions 5-5.2, then you will now be able to get your files back for free using an updated…

Spam email !
Email is both an excellent communication tool and also a way that companies can inform you about their latest products and services. However, email is f…
Searching the Internet !
With ever increasing amounts of material on the internet, virtually any information you need can be found using search engines such as Google and Yahoo!…

5 Cybersecurity Tools Every Business Needs to Know !
Cybersecurity experts all echo the same thing – cyber attacks are going to get more rampant, and they will continue to pose severe threats against…

Backups !
The information held on your computer may be irreplaceable. Regularly backing up your data will ensure that you have more than one copy. The Risks H…

Webmail !
Webmail, such as Hotmail, Yahoo! Mail or gmail – or that supplied by some internet service providers – makes it easy to email using differen…

Software Updates
The software that may be on your computer includes: Microsoft Products (either bundled with the Windows operating system or purchased separately) Of…

Safe Mac Use !
Apple Macs are less vulnerable to attack by malware than PCs. Many people, in fact, believe that Macs are immune to viruses and spyware, but this is def…

Replacing Windows XP !
Despite the frequent introduction by Microsoft of newer versions of its Windows operating system over the years, some business and home PC users are sti…

Online Gaming !
Many computer games are played online against other players over the internet, whether on a console, computer, mobile device or via social networking si…

Avoiding Ratting - Remote Access Trojans
You use your computer or mobile device for many everyday private or confidential tasks, which is why it is essential to take precautions to protect it f…

Remove the Qbit Clean Pro PUP !
What is Qbit Clean Pro PUP? Qbit Clean Pro PUP is a potentially unwanted program that states it scans Windows for Malware/Pup Threats, ways to Enhance …

Remove the Soundrec.exe Miner Trojan !
What is Soundrec.exe Miner Trojan? The Soundrec.exe Miner is a Trojan that uses your computer to mine for the Monero digital currency without your perm…

Remove the Click allow to verify that you are not a robot page !
What is Click allow to verify that you are not a robot Notification Page? If you see a web site that states "Click allow to verify that you are no…

How to Stop Facebook App From Tracking Your Location In the Background !
Every app installed on your smartphone with permission to access location service "can" continually collect your real-time location secretly, …

Remove the Auto PC Cleaner 2019 PUP !
What is Auto PC Cleaner 2019 PUP? Auto PC Cleaner 2019 PUP is a potentially unwanted program that states it scans Windows for Malware/Pup Threats, ways…

Remove the AppSync PUP !
What is AppSync PUP? AppSync is a potentially unwanted program that installs programs on to your computer. These programs include other adware, unwante…

How to Decrypt the Aurora Ransomware with AuroraDecrypter !
The Aurora Ransomware is a Windows infection that encrypts your files and then demands a ransom in bitcoins in order to get the decryption key. This ran…

How to Decrypt the FilesLocker Ransomware with FilesLockerDecrypter !
FilesLocker is a Ransomware as a Service (RaaS) where the developer offers the ransomware executable to "affiliates". These affiliates will th…

How to Decrypt the Stupid Ransomware Family with StupidDecrypter !
Stupid Ransomware is a family of ransomware infections that are typically utilized by less skilled developers and many utilize themes based on movies, p…

How to Decrypt HiddenTear Ransomware Variants !
If you have been infected with a HiddenTear Ransomware variant, then you are in luck as a program called HiddenTearDecrypter has been created by Michael…

Remove the Androidnotif.com Browser Redirect !
What is Androidnotif.com Browser Redirects? A computer is affected by the Androidnotif.com Browser Redirect when your computer is infected with adware …

Remove the Virus Alert from Microsoft Tech Support Scam !
What is Virus Alert from Microsoft Tech Support Scam? The Virus Alert from Microsoft tech support scam is a browser based scam that tries to trick peop…

Remove the Your Windows System is Damaged Scam !
What is Your Windows System is Damaged Scam? The Your Windows system is damaged support scam is a browser based scam that pretends that your Wind…

Remove the SD Downloader Chrome Extension !
What is SD Downloader Chrome Extension? SD Downloader is a Google Chrome extension that has a description of "Please complete the security c…

Remove the Power System Care PUP !
What is Power System Care PUP? Power System Care PUP is a potentially unwanted program that states it scans Windows for Malware/Pup Threats, ways to En…

Remove the StreamHDNow Adware Chrome Extension !
What is StreamHDNow Adware Chrome Extension? StreamHDNow is a Chrome extension that displays advertisements on web pages that you visit. When the adver…

Remove the Media Player Plus PUP !
What is Media Player Plus? Media Player Plus is a potentially unwanted program that allows you play various media files on your computer. Media Player …

Decrypting GandCrab v1, v4, and v5 !
To use the new GandCrab Ransomware decryptor, you need to make sure you have an available copy of the ransom note as it contains a key that will be used…

Remove the Google Chrome User Rewards Scam !
What is Google Chrome User Rewards Scam? The Google Chrome User Rewards is a browser based advertisement that states that you have been selected by Goo…

Remove the You've made the 5-billionth search Advertisement !
What is You've made the 5-billionth search? The "You've made the 5-billionth search" page is an web browser advertisement that states…

Remove the YOUR COMPUTER WAS LOCKED Tech Support Scam !
What is YOUR COMPUTER WAS LOCKED Tech Support Scam? The Your Computer was locked tech support scam is a browser based scam that tries to trick people i…

How to protect yourself from the Dharma Brrr Ransomware !
In order to protect yourself from Dharma, or from any ransomware, it is important that you use good computing habits and security software. First and fo…

How To Check If Your Twitter Account Has Been Hacked !?
Did you ever wonder if your Twitter account has been hacked and who had managed to gain access and when it happened? Twitter now lets you know this. A…

Remove the View.exe PUP !
What is View.exe PUP? View.exe is an potentially unwanted program, or PUP, that is installed by adware bundles. When installed, it will install Chromiu…

Remove the Auto Speedup 2018 PUP !
What is Auto Speedup 2018 PUP? Auto Speedup 2018 PUP is a potentially unwanted program that states it scans Windows for Malware/Pup Threats, ways to En…

Remove the Human Verification Popup !
What is Human Verification Popup? If you are browsing the web and are shown a page titled "Human Verification" that asks you to allow notific…

Remove the Browsing Secure PUP !
What is Browsing Secure PUP? Browsing Secure is an potentially unwanted program that is installed by adware bundles. When installed, a schedule task wi…

Remove the WhiteClick or the White Click Toolbar !
What is WhiteClick or the White Click Toolbar? WhiteClick or the White Click Toolbar is an potentially unwanted program that is installs a toolbar into…

Remove the SATA Monitor or Satamon.exe Trojan !
What is SATA Monitor or Satamon.exe? SATA Monitor, or Satamon.exe, is a Trojan that downloads other malware onto a computer. When installed, an autorun…

Remove the RevServicesX Bitcoin Miner Trojan !
What is RevServicesX Bitcoin Miner Trojan? The RevServicesX Bitcoin Miner is a Trojan that is downloaded and installed onto a computer through other ma…

Remove the WindowsRecoveryCleaner or Iostream.exe Miner !
What is WindowsRecoveryCleaner or Iostream.exe Miner? The WindowsRecoveryCleaner or Iostream.exe Miner is a Trojan that uses your computer to mine for …

Remove the ShutdownTimer or Shutdown Timer PUP !
What is ShutdownTimer or Shutdown Timer PUP? ShutdownTimer or Shutdown Timer is an potentially unwanted program that allows you to set a timer that at …

Remove the Your Computer is heavily damaged Scam !
What is Your Computer is heavily damaged? The Your Computer is heavily damaged Scam is a browser based scam that tries to trick people into thinking th…

Remove the Svchost.exe *32 Miner Trojan !
What is Svchost.exe *32 Miner Trojan? If you see a process called svchost.exe *32 listed in Task Manager and it is utilizing a lot of the CPU, then you…

Remove the FastDataX.exe Trojan !
What is FastDataX.exe Trojan? FastDataX.exe is a Trojan that is commonly downloaded and install by adware bundles and has a digital signature from a co…

Remove the PQwick PUP !
What is PQwick PUP? PQwick is a potentially unwanted program that is commonly installed by adware bundles. When installed, it will display a small over…

emove the XMRig CPU Miner Process !
What is XMRig CPU Miner Process? The XMRig CPU Miner is a legitimate cryptocurrency mining program that is used to mine for cryptocurrency using …

Remove TheSearch Chrome Extension !
What is TheSearch Chrome Extension? TheSearch is a Chrome extension that has a description of "'TheSearch' help you search with a better w…

How to Find Out Everything Facebook Knows About You !
The past few weeks have been difficult for Facebook over concerns that the data of millions of users has been breached. Facebook stores details of almo…

Remove the MessengerPC PUP !
What is MessengerPC PUP? MessengerPC is a potentially unwanted program that opens a window that displays the embedded Facebook Messenger site. Wh…

Mobile Device Security Paper !
This guide should be read alongside the advice set out in the Home Office paper ‘Mobile Device Security: A buyers’ guide to choosing and usi…

How to protect yourself from the Zenis Ransomware !
In order to protect yourself from ransomware in general, it is important that you use good computing habits and security software. First and foremost, y…

Remove the Driver Pro PUP !
What is Driver Pro PUP? Driver Pro is a potentially unwanted program that scans your computer for drivers and then offers updated drivers for detected …

Remove the Kotcatkcomksz Adware !
What is Kotcatkcomksz Adware? The Kotcatkcomksz adware configures a scheduled task that opens up your default browser and automatically connects to an …

How to Remove Gameorplay.info Ads !
What is Gameorplay.info Advertisements? If your computer is connecting to the gameorplay.info and being shown native advertisements for that contain no…

Remove the Page Marker CPU Miner Firefox Addon !
What is Page Marker CPU Miner Firefox Addon? Page Marker is a Firefox addon that will display advertisements in search result pages and web sites that …

Remove the Win an iPhone X Advertisement !
What is Win an iPhone X Advertisement? The "Win an iPhone X" page is an web browser advertisement that states you can win an iPhone X if you …

Remove the Video Control Adware Firefox Addon !
What is Video Control Adware Firefox Addon? Video Control is a Firefox addon that will display advertisements in search result pages and web sites that…

How to remove a Trojan.BitCoinMiner Miner Infection !
What is Trojan.BitCoinMiner? A Trojan.BitCoinMiner is a computer infection that silently runs on your computer while using your CPU or GPU resources to…

How to use Malwarebytes Anti-Malware to scan and remove malware from your computer !
As you may have noticed, MalwareBytes or MBAM, is used in a lot of our removal guides. We do this for no reason other than the fact that the program sim…

Remove the Deftesrg.exe Monero CPU Miner
What is Deftesrg.exe Monero CPU Miner? The Deftesrg.exe Miner is a Trojan that utilizes a victim's computer resources to mine for digital currency …

List of Meltdown and Spectre Vulnerability Advisories, Patches, & Updates !
Two new vulnerabilities called Meltdown and Spectre, or speculative execution side-channel vulnerabilities, have been discovered in modern processors th…

How to protect yourself from the FILE CryptoMix Ransomware !
In order to protect yourself from ransomware, it is important that you use good computing habits and security software. First and foremost, you should a…

Remove the RelevantKnowledge PUP !
What is RelevantKnowledge PUP? RelevantKnowledge is a potentially unwanted program that may displays advertisement and surveys to computer users. This …

How to protect yourself from the File Spider Ransomware
In order to protect yourself from ransomware, it is important that you use good computing habits and security software. First and foremost, you should a…

Remove the Mingc.exe CPU Miner !
What is Mingc.exe CPU Miner? The Mingc.exe Miner is a Trojan that utilizes a victim's computer resources to mine for digital currency. When i…

Remove the YoutubeAdBlock PUP !
What is YoutubeAdBlock PUP? YoutubeAdBlock is a potentially unwanted program, or PUP, that is installed by adware bundles. When installed, this program…

Remove the Tweakerbit Antimalware !
What is Tweakerbit Antimalware ? Tweakerbit Antimalware is a potentially unwanted security program that can be installed via adware bundles. This progr…

How to remove Antivirus 360 (Uninstall Instructions) !
What is Antivirus 360? Antivirus 360 is a rogue anti-spyware program that uses false scan results and aggressive advertising in order to promote itself…

Remove the YourClassifiedsNow Ad Clicking Trojan !
What is YourClassifiedsNow Ad Clicking Trojan? YourClassifiedsNow is a ad clicking Trojan that runs silently in the background on your computer while c…

Some Bad Rabbit Victims Can Recover Files Without Paying Ransom !
Some extremely lucky users will be able to recover files locked by the Bad Rabbit ransomware because of small operational mistakes on the part of the ma…

'Krack' Wi-Fi guidance
What is Krack? Most Wi-Fi networks are configured to encrypt traffic between client devices and access points, so that someone outside the network cann…

True story: What happens when your phone is stolen (video) !
Film student Anthony van der Meer decided to find out what happens to stolen telephones and the data on them. He created a 20-minute documentary …

How to remove Tech Support Scam Popups in your Browser !
What is Tech Support Scam Popups? A Tech Support Scam browser popup is when your browser displays an advertisement that pretends to be from Microsoft, …

Remove the Floxif CCleaner Trojan
What is Floxif CCleaner Trojan? Floxif is the detection for a Trojan that was bundled with a hacked version of CCleaner. Downloads of the 32-bit versio…

CCleaner Malware Incident - What You Need to Know and How to Remove
This is a small guide and FAQ on the malware installed alongside CCleaner 5.33.6162. For a full recap of what happened, you can read our complete CClean…

Remove the Microsoft Windows Product Key Tech Support Scam
What is Microsoft Windows Product Key Tech Support Scam? The Microsoft Windows Product Key Tech Support Scam is a Trojan.Tech-Support-Scam that display…

Remove the Your Computer May Have a Virus Web Page !
What is Your Computer May Have a Virus Web Page? The Your Computer May Have a Virus Scam Popup is a web browser advertisement shown by affiliates promo…

Remove the "Novo Optimizer GPU Miner"
What is Novo Optimizer GPU Miner? The Novo Optimizer GPU Miner is a Trojan that utilizes a victim's GPU, or Graphic Processing Unit, to mine digita…

Remove the Your Windows computer is at High Risk Popup !
What is Your Windows computer is at High Risk Popup? The Your Windows computer is at High Risk Popup is a web browser advertisement shown by scammy rem…

10 Tips to Prevent Phishing Attacks
Have you ever considered that you could be a target for phishing attacks? It’s not a new issue, but it’s a rising threat. Phishing attacker…

How to remove the Windows Security Warning Popup Scam !
What is Windows Security Warning Popup Scam ? The Windows Security Warning Scam Popup is a web browser advertisement shown by scammy remote tech suppor…

Remove the Oneway Hosts File Modifying Trojan !
What is Oneway Hosts File Modifying Trojan? OneWay is a Trojan that modifies the Windows HOSTS file so that the computer is not able to reach various a…

Remove the Your Windows is infected Popup Scam !
What is Your Windows is infected Popup? The Your Windows is infected Popup is a browser based tech support scam that tries to scare visitors into think…

Remove the WindowService Trojan !
What is WindowService Trojan? The WindowService Trojan is malware program that is commonly installed by adware bundles that you download from the Inter…

The best free parental control software 2017 !
Keep your children safe online with the best free parental control software for Windows. It's hard to imagine anything less child-friendly than an …

Remove The publisher has been blocked from running software Alert ?!
What is The publisher has been blocked from running software Alert? If you are receiving errors when you try to install or run a security program that …

How to Remove Smart Registry Care ?
What is Smart Registry Care? Smart Registry Cleaner is a Registry cleaner that scans for a variety of categories that include ActiveX/COM, System Softw…

How to remove the WannaCry and Wana Decryptor Ransomware !
This section will provide a brief tutorial on how to remove WannaCry/Wana Decryptor using MalwareBytes and Emsisoft. While both can remove this infectio…
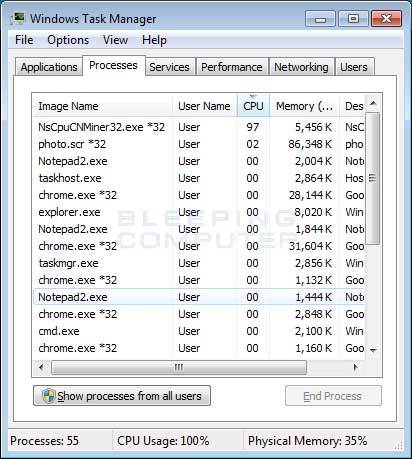
Remove the Photo.scr Monero Miner
What is Photo.scr Monero Miner? The Photo.scr Miner is a Trojan that utilizes a victim's computer processing power to mine the digital currency cal…

How to remove Fake Java Update PopUps !
What is Fake Java Update PopUp? The Fake Java Update PopUp is a web browser advertisement shown by scammers that are trying to trick you into downloadi…

Remove the "FilePlus" Potentially Unwanted Program
What is FilePlus? FilePlus is a program that allows you to download copyrighted movies, tv shows, and programs for free. What it does not tell you, tho…

Remove the MaohaWiFi Program (Uninstall Guide)
MaohaWiFi is a potentially unwanted program that is commonly bundled with free programs that you download from the Internet. This programs allows your c…

Remove AdBlocker for YouTube !
What is AdBlocker for Youtube? AdBlocker for Youtube is a potentially unwanted Google Chrome extension that states that it blocks advertisements shown …

"CryptorBit" and "HowDecrypt" Information Guide and FAQ
Table of Contents: How to get help with CryptorBit What is CryptorBit or the HowDecrypt Ransomware How to recover files encrypted by CryptorBit Ho…

How to remove Unwanted Chromium Browsers ?!
What is Chromium Browser? Chromium is a open source web browser created by Google, which Google Chrome is based on. As Chromium is open source, it can …

Remove the MSSecTeam Tech Support Scam (Removal Guide)
What is MSSecTeam Tech Support Scam? The MSSecTeam Tech Support Scam is a Trojan.Tech-Support-Scam that displays a lock screen pretending to be from Mi…

This PC Has Been Blocked Screenlocker Removal Guide !!
What is This PC Has Been Blocked Screenlocker? The This PC Has Been Blocked screen locker is a Trojan that displays a fake security screen stating that…

How to use SUPERAntiSpyware to scan and remove malware from your computer !
With viruses, worms, Trojans, and malware becoming more and more pervasive in every computer users life, it is important to have an arsenal of tools tha…

PacketTotal - A Useful Site for Analyzing PCAP Files
If you are InfoSec professional who commonly deals with intrusion detection and response or malware analysis, a new site called PacketTotal may make you…

Locky Ransomware Information, Help Guide, and FAQ!
What is the Locky Ransomware? Locky is a Windows ransomware infection that was released in the middle of February 2016. This ransomware infection will a…

Remove the BrowserMe.exe or Chrome_Font.exe Fleercivet Ad Clicker Trojan !
The "BrowserMe" or "Chrome_Font.exe" Trojan is a computer infection that only targets users of the Chrome browser. When running it w…

Top tips for protecting your Android from malware !
With the largest installed base of all operating systems, Android has certainly taken the mobile world by storm, and as the active user stats show, Andr…

How to tell if your Snapchat has been hacked, and how to get it back !
What to look out for, and what to do about it! Snapchat is one of the most popular messaging services available today. As of June 2016, more than 150 …
Padlock Screen Locker Removal Guide
The Padlock Screen locker is a Trojan that displays a picture of a locked door with a message stating that the victim's files have been deleted and …
How to Remove Antivirus 10 (Removal Guide)
Antivirus 10 is a scareware program that pretends to an anti-virus program, but in reality is just a Trojan trying to scare you into purchasing it. This…
CryptorBit and HowDecrypt Information Guide and FAQ
CryptorBit and HowDecrypt Information Guide and FAQ

CryptoLocker Ransomware Information Guide and FAQ
Info: The original CryptoLocker infection was disabled on June 2nd, 2014 when Operation Gameover took down its distribution network. Since then there ha…

How to Protect and Harden a Computer against Ransomware ?!
2016 is almost over and it definitely taught us one thing; Ransomware is here to stay and it's only going to get worse. With even the smaller ransom…
Using Wireless Technology Securely
In recent years, wireless networking has become more available, affordable, and easy to use. Home users are adopting wireless technology in great number…
PGP KEY MANUAL
PGP KEY MANUAL

777 Ransom
Trend Micro Ransomware Decryptor is designed to decrypt files encrypted by 777 Ransom. For more information please see this how-to guide. Download.

Free decryptor released for Atom Silo and LockFile ransomware!
Avast has just released a decryption tool that will help AtomSilo and LockFile ransomware victims recover some of their files for free without having to…

Kali Linux 2021.3 released with new pentest tools, improvements!
Kali Linux 2021.3 was released yesterday by Offensive Security and includes a new set of tools, improved virtualization support, and a new OpenSSL confi…

Nikto
Nikto is one of the best cybersecurity tools that conduct web vulnerabilities. Nikto too is an open-source tool. The tool is widely employed by cybersec…

Qualys BrowserCheck
Qualys BrowserCheck is a cloud service that lets you check if your browser and installed plugins are all up-to-date so that you not affected by security…

Nmap!
Nmap ("Network Mapper") is a free and open source (license) utility for network discovery and security auditing. Many systems and network admi…

CISA releases tool to review Microsoft 365 post-compromise activity!
The Cybersecurity and Infrastructure Security Agency (CISA) has released a companion Splunk-based dashboard that helps review post-compromise activity i…

This new Microsoft tool checks Exchange Servers for ProxyLogon hacks!
On March 2nd, Microsoft released out-of-band emergency security updates to fix four zero-day vulnerabilities actively used in attacks against Microsoft …

Specops Password Auditor
Authentication and password security is more important than ever. Our password audit tool scans your Active Directory and identifies password-related vu…

Ziggy ransomware decryption keys
The Ziggy ransomware operation has shut down and released the victims' decryption keys after concerns about recent law enforcement activity and guil…

Sophos Home
Sophos Home is a free Internet security product that protects Windows and Mac computers from malware and malicious web sites. Sophos Home can be install…

ProtonVPN !
When you use ProtonVPN to browse the web, your Internet connection is encrypted. By routing your connection through encrypted tunnels, ProtonVPN's a…

CISA releases Azure, Microsoft 365 malicious activity detection tool!
The Cybersecurity and Infrastructure Security Agency (CISA) has released a PowerShell-based tool that helps detect potentially compromised applications …

DNSTwist
DNSTwist is a free program that allows you to detect phishing, typosquatters, and attack domains that are based on an inputted domain. If you are a site…

have i been pwned?
Check if you have an account that has been compromised in a data breach Read more.

Azure Defender for IoT
Azure Defender for IoT is an IoT/OT device threat protection solution that integrates with Microsoft's Azure Sentinel and third-party solutions (SIE…

haveibeenEMOTET !
haveibeenEMOTET is a free service made to check if your email address or domain is involved in the Emotet malspam (name@domain.ext or domain.ext). Your …

ThunderX Decryptor
ThunderX is a relatively new ransomware that became active towards the end of August 2020. ThunderX Decryptor is designed to decrypt files encrypt…

Zenscrape!
Web scraping, or also known as web data extraction, is the process of recouping or sweeping data from web-pages. It is a much faster and easier process …

EmoCheck
Emotet detection tool for Windows OS. Download EmoCheck

Spybot!
If you suspect that you have spyware installed on your computer, then an excellent tool called Spybot - Search and Destroy can be used to remove them. W…

Bloatbox
Bloatbox allows Windows 10 users to debloat the operating system by removing unwanted preinstalled apps. Download Bloatbox

Avast Secure Browser for Windows!
Avast Secure Browser strives to offer a ‘private, fast and secure service for Windows users. Simply put, this product has been built for privacy b…

Google Password Manager
Manage your saved passwords in Android or Chrome. They’re securely stored in your Google Account and available across all your devices. Read more…

Windows File Recovery
Accidentally deleted an important file? Wiped clean your hard drive? Unsure of what to do with corrupted data? Windows File Recovery can help recover yo…

Google Family Link for Parents

Firefox Private Network
Firefox Private Network is a browser extension by Firefox. It hides your browsing activity and IP address by rerouting your digital footprint through th…

Cisco AnyConnect Secure Mobility Client!
Companies often require people to work from home using a secure network. Cisco AnyConnect Secure Mobility Client provides this through a mobility centri…

ImmuniWeb AI Platform
ImmuniWeb released a new free tool to monitor and measure an organization's exposure on the Dark Web. ImmuniWeb AI Platform is a free tool that craw…

Ad Guardian Plus
Ad-blocker and anti-malware software Ad Guardian Plus is a security and privacy software that blocks online advertisements from appearing on websites or…

Shade Ransomware Decryptor!
Kaspersky has released an updated decryptor for the Shade Ransomware (Troldesh) that allows all victims who have their files encrypted to recover them f…

TouchVPN !
TouchVPN for Windows is a VPN service for computers running Windows 10. It can also be installed in Mac OS X, Android, and iOS devices. TouchVPN can he…

Qualys BrowserCheck!
Qualys BrowserCheck is a cloud service that lets you check if your browser and installed plugins are all up-to-date so that you not affected by security…

AppTrana Offers Protection to Online Businesses During Coronavirus Outbreak !
These are unprecedented times, and everyone is going through a testing period, with more than 3 billion people locked down all over the world. Business…

List of Free Software and Services During Coronavirus Outbreak!
In response to the Coronavirus (COVID-19) outbreak, many organizations are asking their employees to work remotely. This, though, brings new challenges …

Shodan !
Shodan is an IOT testing tool which you can use to discover which of your devices are connected to the Internet. It allows you to keep track of all the …

Aircrack-ng
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture…

I Got Phished
I Got Phished is a new service from malware and malicious activity monitoring site Abuse.ch that currently has a database of over 3,400 compromised emai…

Safe Pad
Safe Pad encrypts your document using industrial-grade AES encryption, making it perfect for storing banking or credit card details. Users have the opti…

FileZilla !
FileZilla is open source software distributed free of charge under the terms of the GNU General Public License. FileZilla Client is a fast and reliable …

XpoLog
XpoLog automates the entire log management lifecycle: collection, parsing, analysis, monitoring, problem discovery. Download XpoLog.

New BlueKeep Scanner Lets You Find Vulnerable Windows PCs !
A new scanning tool is now available for checking if your computer is vulnerable to the BlueKeep security issue in Windows Remote Desktop Services. Des…

Ad-aware Antivirus Free
This software not only provides the best free protection for your PC but also provides real-time protection and download protection. To get complete pro…

NetAdapter Repair All In One !
NetAdapter Repair All In One is a utility that acts as a Swiss army knife for network related Windows tasks. Not only can NetAdapter Repair be use…

Website Security Test
Website Security Test është një produkt falas i disponueshëm në internet, i siguruar dhe administruar nga "ImmuniWeb"…

Malwarebytes 4.0
Malwarebytes has released version 4.0 of their flagship antivirus product and with it comes a new scanning engine, a new user interface, threat statisti…

Paradise Ransomware Decryptor
A decryptor for the Paradise Ransomware has been released by Emsisoft that allows victims to decrypt their files for free. For over two years, the Para…

Emsisoft Decryptor for STOP Djvu
The STOP Djvu ransomware encrypts victim's files with Salsa20, and appends one of dozens of extensions to filenames; for example, ".djvu",…

Nemty Ransomware Decryptor
Victims of the Nemty Ransomware finally have something to be happy about as researchers have released a decryptor that allows them to recover files for …

Emsisoft Decryptor for Muhstik Ransomware
The Muhstik Ransomware encrypts files on compromised QNAP systems using AES-256, and adds the extension ".muhstik" to files. Download the dec…

Grendel
Scan web application security tool for finding security vulnerabilities; features are also available for manual penetration testing. Read more.
Burp Suite !
If you’re looking to perform automated vulnerability scanning of web apps, you NEED to check out burp suite. The tool uses numerous componen…

THOR FREE !
Software updater for Windows PCs We automate your software updates to improve your security. THOR FREE keeps your vulnerable applications up to date au…

EULAlyzer
EULAlyzer discovers if the software you're about to install displays pop-up ads, transmits personally identifiable information, uses unique identifi…

ECh0raix Ransomware Decryptor !
eCh0raix is a ransomware that has been targeting QNAP NAS devices since June 2018 by brute forcing passwords and exploiting vulnerabilities in order to …

Redirect Detective !
What is Redirect Detective? Redirect Detective is free tool that allows you to do a full trace of a URL Redirect. It will show you the complete path a…

LOOCIPHER DECRYPTOR
LooCipher encrypts the victim's files using AES-128 ECB, and adds the extension ".lcphr". No ransom note file is left, but the malware do…

BreachAlarm !
What’s BreachAlarm all about? BreachAlarm tells you if you need to change passwords.BreachAlarm is a service that allows you to check anonymously…

Nessus !
Nessus is a vulnerability scanner of choice. It allows you to perform thorough scans of a network to identify vulnerabilities. The home edition is free …

"GandCrab" Ransomware Decryptor !
GandCrab is one of the most prolific families of ransomware to date that has infected over 1.5 million computers since it first emerged in January 2018.…

pyLocky Decryptor
The pyLocky decryptor will decrypt files encrypted by version 1 and 2 of the ransomware. Supported encrypted file extensions for version 1 are .lockedfi…

Redirect Detective !
Redirect Detective is free tool that allows you to do a full trace of a URL Redirect. It helps you analyze short links to determine if they actually dir…

Emsisoft Decrypter for JSWorm 2.0
JSWorm 2.0 is a ransomware written in C++ that uses Blowfish to encrypt files, and adds the extension ".[ID-numbers][email].JSWORM" to files. …

AdBlocker !
If you want to improve the security of your internet usage, you should look into AdBlock. Not only will it filter out those annoying ads, it will protec…

ModSecurity !
ModSecurity is the “Swiss Army Knife” of web application firewalls. If you are a web application developer, you must look into this tool. It…

Emsisoft Decrypter for MegaLocker !
MegaLocker encrypts a victim's files using AES-128 ECB, and adds the extension ".nampohyu" to files. The ransom note "!DECRYPT_INSTRU…
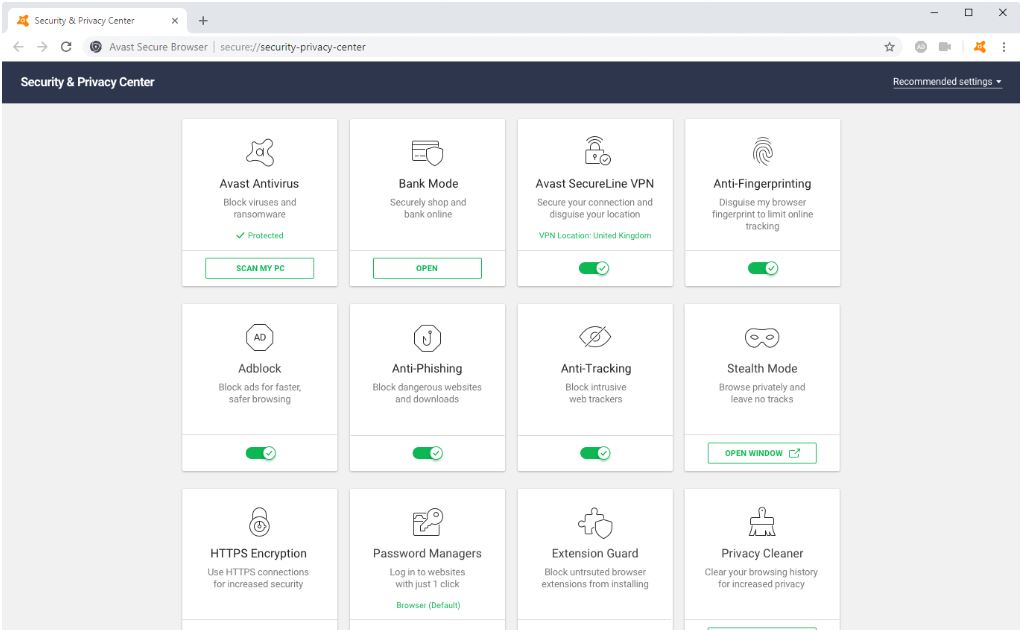
Avast Secure Browser !
Avast Secure Browser strives to offer a ‘private, fast and secure’ service for Windows users. Simply put, this product has been built for pr…

Trend Micro Maximum Security !
Trend Mirco Maximum Security strives to deliver complete protection for all the ways that its users connect. Providing powerful protection for up to 10 …

Stellar
Stellar recovers documents, emails, photos, videos, and audio files, etc. from any storage media— hard drives, fusion drives, SSDs, SD cards, USB …

AuroraDecrypter
AuroraDecrypter is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the Aurora Ransomware. Using this decryptor, vic…

FilesLockerDecrypter !
FilesLockerDecrypter is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the FilesLocker Ransomware. This decrypter …

Hidden Tear Decrypter
Hidden Tear Decrypter is a free decryption program created by Michael Gillespie that allows you to decrypt files encrypted by Hidden Tear Ransomware var…

Tweaking.com Technicians Toolbox!
"Tweaking.com Technicians Toolbox" is a free suite of administration tools and system monitors that allows a user to quickly perform diagnosti…

ProtonVPN Plus !
Due to a drastic increase in cyber attacks on personal computers and networks over the past few years, there are hundreds of VPN services to choose from…

Sygate Personal Firewall !
Free for personal use, Sygate Personal Firewall provides best of breed security in a user friendly interface, protecting your PC from hackers, trojans a…

777 Ransom
Trend Micro Ransomware Decryptor is designed to decrypt files encrypted by 777 Ransom. For more information please see this how-to guide.

GandCrab Ransomware decryption tool
Bitdefender released the world’s first decryption tool to help GandCrab ransomware victims get their data back for free. But since then, victims o…

GMER !
GMER is a simple yet powerful anti-malware tool that thoroughly scans your system for vulnerabilities and evidence of Rootkit activity. It has a standar…

Comodo Antivirus !
Comodo Antivirus is a solid, reliable array of tools that provides a reassuring level of security for Microsoft Windows based computers. It provides qu…

Sunbelt Personal Firewall
Protect yourself from hackers. Secure your PC with a 100% free firewall download. Sunbelt Personal Firewall (SPF), previously known as Kerio Firewall, w…

AntiLogger
AntiLogger protects every application on your computer, not just your web browser. The application stops keyloggers by scrambling every key that you typ…

GridinSoft Anti-Malware
GridinSoft Anti-Malware (formerly Trojan Killer) is a specialised app that is designed to target numerous different types of malware, including PUPs, sp…

HMA! Pro VPN
HMA! Pro VPN is a leading internet encryption service based on virtual private network technology. Whilst VPN’s are predominantly used to remotely…

360 Total Security !
Qihoo's 360 Total Security is a free antivirus program that offers virus scanning using their own proprietary engine as well as ones from BitDefende…

Free Thanatos Ransomware Decryption Tool !
If your computer has been infected with Thanatos Ransomware and you are searching for a free ransomware decryption tool to unlock or decrypt your files&…

Panda Free Antivirus
Panda Free Antivirus is one of many free antivirus programs working to distinguish itself from the herd -- and with a history stretching back to 1990, t…

Speccy!
Speccy is a comprehensive, lightweight, advanced system information tool for your PC. It provides you with detailed statistics on every piece of hardwar…

Avast Free Antivirus
Avast Free Antivirus is an efficient and comprehensive antivirus program. It is one of the most popular antivirus programs available, thanks to the reli…

FixExec !
FixExec is a program that is designed to fix executable file associations for the .bat, .exe, and .com file extensions. If the program detects any of th…

AVG AntiVirus FREE
AVG AntiVirus FREE is AVG’s brand new product for ensuring your safety and security online. It is powerful, feature rich, and has a newly designed…

Advanced IP Scanner
Advanced IP Scanner is a free, fast and powerful network scanner with a user-friendly interface. In a few seconds, Advanced IP Scanner can locate all th…

Bitdefender Antivirus Free Edition
The perfect way to keep your PC, Mac or Android device protected if you don’t want to have to think about ongoing maintenance. It offers superior…

BitKangarooDecrypter
BitKangarooDecrypter is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the BitKangoroo Ransomware. Using this decr…

InsaneCrypt (desuCrypt) Decrypter!
InsaneCrypt Decryptor is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the desuCrypt Ransomware variant that appe…
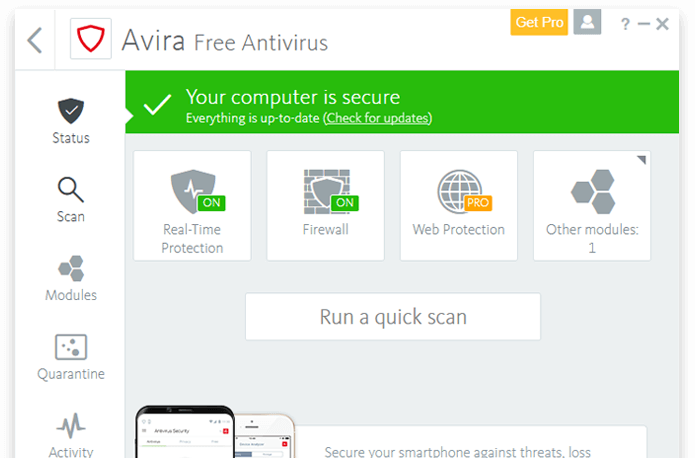
Avira Free Antivirus
Avira Free Antivirus is a free anti-malware, anti-ransomware and anti-virus program for Windows devices. It is a light security program that is easy to …

McAfee Stinger
McAfee Stinger is a standalone utility that is designed to target and remove specific computer infections and viruses. This program is not an anti-virus…

Rem-VBSworm
Rem-VBSworm is a utility that removes VBS and Windows Script Host malware from your computer, USB drives, and the network. This program was create…

"Jigsaw Decrypter"
Jigsaw Decryptor is a free decryption program created by Michael Gillespie for variants of the Jigsaw Ransomware. Using this decryptor a victim of the J…

GPU-Z 2.7.0
GPU-Z is a free tool that provides detailed information on the graphics cards in your computer. Using this tool you can see information such as the GPU …

McAfee Real Protect !
McAfee Real Protect is a real-time behavior program that monitors your computer for suspicious activity. Real Protect utilizes machine learning and beha…

Crypt38Decrypter !
"Crypt38 Decrypter" is a free decryption program created by Michael Gillespie for the Crypt38 Ransomware. Using this decryptor a victim of the…

Simple System Tweaker 2.2.0
Simple System Tweaker is a free utility that optimizes various functions in Windows. These tweaks could allow for faster boot and shutdown times, faster…

Autoruns 13.71
Autoruns is a free Sysinternals tool from Microsoft that enumerates all the programs that automatically start on a Windows machine. You can then e…

Offline CryptoMix Ransomware Decryptor
Avast released a decryptor for CryptoMix victim's that were encrypted while in offline mode. Offline mode is when the ransomware runs and encrypts a…

UCheck
UCheck is a free program that allows you to scan a computer for outdated programs and automatically update them to the latest version. UCheck also…

VT Hash Check 1.60
"VT Hash check" adds a context menu item for all files allowing you to quickly search VirusTotal.com for matching files and their correspondin…

Shortcut Cleaner 1.4.9.0
Shortcut Cleaner is a utility that will scan your computer for Windows shortcuts that have been hijacked by unwanted or malicious software. When S…

GIBON Ransomware Decryptor
"GibonDecryptor" is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the GIBON Ransomware. Using this decr…

RansomNoteCleaner !
Ransom Note Cleaner is a program that can be used to scan a ransomware victim's computer for left over ransom notes and elete them. When someone is …

Chrome Cleanup Tool
The Chrome Cleanup Tool is a program written by Google that will scan a computer for programs that cause problems in Google Chrome. The targeted applica…

Symantec Kovter Removal Tool
The Symantec Kovter Removal Tool can be used to remove the Kovter infection from your computer. The Kovter infection is a Click Fraud Trojan as it…

Malwarebytes Anti-Exploit 1.10.1.41
Malwarebytes Anti-Exploit is a security program that protects you from zero-day exploits that target browser and application vulnerabilities. This progr…

Sophos Home
"Sophos Home" is a free Internet security product that protects Windows and Mac computers from malware and malicious web sites. Sophos Home ca…

WinPatrol
WinPatrol is a free security utility that allows you to get a closer look under the hood of Windows so that you can detect programs that should not be r…

PowerLockyDecrypter
"PowerLocky Decrypter" is a free decryption program created by Michael Gillespie for the PowerWare Locky Ransomware. Using this decryptor a vi…

Process Monitor (ProcMon)
Process Monitor, or ProcMon, is an advanced monitoring tool that allows you to see in real-time the file system, registry, and process activity occuring…

BTCWareDecrypter Download !
BTCWareDecrypter is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the BTCWare ransomware. Using this decryptor, v…

RansomFree Download !
Cyberreason's RansomFree is a ransomware protection program that silently runs in the background looking for ransomware activity on a computer. If a…

"Malwarebytes Anti-Ransomware 0.9.18.807" Download !
Malwarebytes Anti-Ransomware Beta is a program that protects your computer from file encrypting ransomware programs. This programs quietly sits in…

StrikedDecrypter
StrikedDecrypter is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the Striked Ransomware. Using this de…

Mole02 Decryptor Download !
Mole02 Decryptor is a program that allows victims who have been encrypted the Mole02 Ransomware to recovery their files for free. This decryptor is very…

DCryDecrypter 1.0.0.1 Download !
DCryDecrypter is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by the DCry Ransomware. Using this decryptor, victims…
PC Hunter 1.51 Download
"PC Hunter" is a very powerful security utility that allows great insight into the inner workings of Windows. It is especially useful when you…

Farbar Recovery Scan Tool Download
Farbar Recovery Scan Tool, or FRST, is a portable application designed to run on Windows XP, Windows Vista, Windows 7 and Windows 8 in normal or safe mo…

AVCertClean 0.3 Download
A recent infection blocks the launch of several security software by setting their code signing certificate as untrusted. This software will search for…

VIPRE Advance Security for Home Download !
COMPANY'S DESCRIPTION: With today’s online threats, you can’t afford to settle for anything but the best. The top-rated, award-winning …

Glasswire 1.2.3100.0 Download
GlassWire is a free network monitoring tool that displays and alerts you about the network traffic originating from your computer. This allows you…

StupidDecryptor Download
StupidDecryptor is a ransomware decryptor created by Michael Gillespie that decrypts files encrypted by various ransomware infections that are based off…

AVG Remover Download
AVG Remover allows you to completely uninstall detected AVG products from your computer. Unfortunately, there are times when the traditional metho…

RakhniDecryptor Ransomware Decryptor Download !
RakhniDecryptor is a general purpose ransomware decryptor created by Kaspersky Labs. Instead of creating a separate decryptor for each ransomware infect…

Zemana AntiMalware Download
Zemana AntiMalware is a second opinion cloud based malware scanner that allows you to perform on demand scanning as necessary. Zemana AntiMalware does n…

RogueKillerCMD Download
RogueKillerCMD is the command line version of the RogueKiller anti-malware program and security utility. This program is designed to be used by power us…

RogueKiller Download
RogueKiller is a security tool that can be used to terminate and remove malicious processes and programs from your computer. RogueKiller has the a…

CryptoSearch Download
CryptoSearch is a utility created by Michael Gillespie that allows you to clean up your computer of encrypted files and ransom notes from a ransomware i…
CryptON Ransomware Decryptor Download
If you are infected with the CryptON Ransomware, then you are in luck. Emsisoft was able to figure out a way to decrypt files encrypted by this ransomwa…

SUPERAntiSpyware Download
SUPERAntiSpyware is a free anti-spyware program that offers excellent detections and quick removal of common infections. As malware is constantly evolvi…

Junkware Removal Tool 8.1.0.0 Download
Junkware Removal Tool is a security utility that searches for and removes common adware, toolbars, and potentially unwanted programs (PUPs) from your co…

Windows Repair (All In One) 3.9.25 Download
Windows Repair is a utility that contains numerous mini-fixes for Windows. This tool will allow you to repair common issues with your computer suc…

Heimdal Free Download
Heimdal Free is a program that scans your computer for outdated and possibly vulnerable programs and automatically updates them to the latest version fo…

EMSISOFT HIJACKFREE
Emsisoft HiJackFree is a simple tool that allows detection of malicious activity and allows the user to stop them. Using tools is possible to get an ins…

Malwarebytes Anti-Malware
Malwarebytes' is an important security program for any computer user to have installed on their computer. It is light-weight, fast, and best of all,…

RKill
RKill is a program that was developed at BleepingComputer.com that attempts to terminate known malware processes so that your normal security software c…
BitStakDecrypter Download
BitStak Decrypter is a free decryption program created by Michael Gillespie for the BitStak Ransomware. Using this decryptor a victim of the BitStak Ran…
HEIMDAL FREE
FREE HEIMDAL security software tool applied in 20 most used software applications in the world. Performs these functions: Scans your computer every 2…

ComboFix
ComboFix is a program, created by sUBs, that scans your computer for known malware, and when found, attempts to clean these infections automatically. In…

AdwCleaner
AdwCleaner is a program that searches for and deletes Adware, Toolbars, Potentially Unwanted Programs (PUP), and browser Hijackers from your computer. &…


Emsisoft Emergency Kit
The Emsisoft Emergency Kit contains a collection of programs that can be used without software installation to scan for malware and clean infected compu…
Microsoft Safety Scanner
Trend Micro Ransomware File Decryptor
Direct Links
Mission
National Unit “KOS-CERT” will have a key role in maintaining the networks security and electronic communications services of the Republic of Kosovo. The purpose and mission is to help the community to cope effectively with the challenges of cyber security, coordination of actions in order to solve cyber security incidents and effectively prevent them.
Community
“KOS-CERT” community includes all operators that are authorized / licensed by the Regulatory Authority of Electronic and Postal Communications (TRA) to provide networks and electronic communications services and the consumers who use these networks and / or services in the Republic of Kosovo.






